How To Provide Equal Broadband Internet Access For All
By Duane Thresher, Ph.D. December 25, 2022
In memory of my father, who was a U.S. Air Force officer in time of war, including being an Atlas ICBM silo officer during the Cuban Missile Crisis of the Cold War and an aircraft officer in Saigon right before the Tet Offensive in the Vietnam War. After retiring to his rural home, he waited 25 years for real broadband Internet access but never got it, even while government and business promised it all those years.
If you are an investor who would really like to help America by doing something about its increasingly inadequate infrastructure, so probably not an ESG investor, and an investor who understands that All Cryptocurrencies Might As Well Be Tulip Bulbs, then the best answer to How To Provide Equal Broadband Internet Access For All is to see Wanted: Visionary Investors for Historic Business Plan, contact me, and then read

How To Defend Against Electrical Grid Attacks
By Duane Thresher, Ph.D. December 7, 2022
In memory of the 2,403 Americans who were killed in the sneak attack on Pearl Harbor on December 7, 1941.
If you are an investor who would really like to help America by doing something about its decaying and insecure infrastructure, so probably not an ESG investor, and an investor who understands that All Cryptocurrencies Might As Well Be Tulip Bulbs, then the best answer to How To Defend Against Electrical Grid Attacks is to see Wanted: Visionary Investors for Historic Business Plan, contact me, and then read

Apscitu Warned of Google Censoring Republican Email Ads Already in 2012 Presidential Election
December 2, 2022Google Mail (Gmail) is the most popular email service by far, used by millions of individuals, government, media, business, and academia for years.
However, only very recently have politicians and the media, all IT incompetent, started warning of Google, via its Gmail spam filter, censoring Republican email ads in recent elections, particularly the 2020 Presidential Election. But over 3.5 years ago, in Google: Invasion of the Email Snatchers, Apscitu warned of this having already happened in the 2012 Presidential Election:

Cryptocurrency Crisis: All Cryptocurrencies Might As Well Be Tulip Bulbs
By Duane Thresher, Ph.D. November 17, 2022
Cryptocurrency is IT; information technology, in case you forgot. Cryptography, from whence cryptocurrency gets its name, is the technology of encrypting/decrypting information; see Incompetent Encryption Is Worse Than No Encryption.
The name "cryptocurrency" is not because transactions with it are secret, which is decidedly not the case (see ahead). And while who is involved in the transactions can be hard to find, particularly if one transactor is in another country, like Russia (see ahead), if one of the transactors wants to exchange the cryptocurrency for real money (dollars) in the U.S., it is not that hard to find them; see for example the Update at the end of Apscitu Warned of Twitter Hacking Two Years Ago, where the hackers got payment in Bitcoin and were then easily identified and caught.

Twitter vs. Mastodon, Free Speech vs. Free Software
By Duane Thresher, Ph.D. November 14, 2022
In late October 2022, just before Halloween, Elon Musk, in a mammoth act of free speech activism, bought out Twitter Inc. for $44 billion, taking the corporation private and taking over control, including dissolving the board of directors. Ever since then, the frightened woke media and frightened woke companies have been trying to make Twitter fail, so they can continue to control speech, and thus thought/opinion/votes.
I myself noted and complained about the woke Wall Street Journal (WSJ) newsroom trying to make Twitter fail, in violation of SEC rules (see Banned-For-Life Trader and Business Insider CEO Henry Blodget Using Fake News for Stock Price Manipulation? and Stock Market Crash Deja Vu: Reddit Violates Securities Exchange Act).

Roe v. Wade Was Hacked — Justice Is Blind And IT Incompetent
October 31, 2022Sometime between February 2022, when Supreme Court Justice Samuel Alito circulated among the justices a draft majority opinion in Dobbs v. Jackson Women's Health Organization that overturned Roe v. Wade, and early May 2022, when Politico illegally published it, someone somehow stole this document. Following the surprise document publication, unprepared-for widespread domestic strife ensued, including an assassination attempt on Supreme Court Justice Brett Kavanaugh.
Chief Justice John Roberts directed the Marshal of the United States Supreme Court, Gail Curley, to investigate and find those responsible. (Even if it were not incompetent and corrupt, the FBI is not allowed to investigate; the Supreme Court has its own police, with the Marshal as head.) To date, after almost 9 months, a full-term pregnancy, those responsible for the theft have still not been found.

Corruption and Free Speech at Columbia
By Duane Thresher, Ph.D. October 10, 2022
These days, with Twitter and Facebook being hotbeds of censorship, IT and free speech are intimately related. I am an expert in both, although less willingly so for the latter, since I became so through denial of my free speech. My denial occurred at another hotbed of censorship these days, universities, and via a major method for censorship, email. This denial of free speech goes hand in hand with corruption at the universities, as it does for government.
This article, particularly its title, Corruption and Free Speech at Columbia (today is Columbus Day), is with acknowledgement to God and Man at Yale by William F. Buckley, who was essentially also writing about corruption and free speech (his book is subtitled The Superstitions of "Academic Freedom") at a university, Yale, while he was a student there, graduating in 1950. (Today Yale denies free speech to the point where some federal judges will no longer accept Yale Law School graduates as law clerks.)

Wanted: Visionary Investors for Historic Business Plan
July 20, 2022For the last few months I (Duane Thresher, Ph.D.) have been working on a historic business plan that will greatly expand what Apscitu Inc. does. I thus have had little time for working on articles. Further, I will now be pitching the business plan to investors and will again have little time for working on articles.
The business plan title is:

Russia and Restaurant Manager Bonnie Titone Duke IT Out Over Forced Meltdowns of Carolina Nuclear Power Plants
By Duane Thresher, Ph.D. January 28, 2022
As I have written, in Nuclear 9/11 for example, Russia, led by President Vladimir Putin, would love to attack the U.S. by hacking into nuclear power plants and forcing meltdowns, since it would prove that a catastrophic meltdown like Chernobyl in 1986 can't only happen to them. As it did in the hacking and ransomwaring of Colonial Pipeline (see U.S. Surrenders in IT War, Starts Paying Tribute to Russia), Russia will do this by determining the IT incompetent, regardless of sex or race (i.e. diversity), of those who are supposed to protect us from such cyberattacks — e.g. Chief Information Officers (CIOs) of nuclear power plants — and hacking into and forcing meltdowns of those insecure nuclear power plants. IT incompetent Marie Mouchet is the hacked woman CIO of Colonial Pipeline, and before that she was CIO of Southern Nuclear, which operates three nuclear power plants in Georgia and Alabama; IT incompetent Martin Davis is the black CIO of Southern Nuclear now (see also Ransomwared Nuclear Power Plants Upwind of Major U.S. Cities). Lest this be taken as a condemnation of the South, I wrote in Hacking and Forced Meltdown of Nuclear Power Plants: Upwind of Washington, Baltimore, Philadelphia about IT incompetent woman CIO Kelly Lyman of PECO, which operates the notoriously insecure Peach Bottom nuclear power plant in Pennsylvania. Here I write about IT incompetent — she only has a BS in restaurant management — Bonnie Titone, who is the woman CIO of Duke Energy, which operates six nuclear power plants spread throughout some of the most densely populated areas of North and South Carolina. Forced meltdowns of these old and already-unsafe nuclear power plants, and the resulting spread of radiation by wind and water, could horribly kill hundreds of thousands by radiation sickness. Apscitu can prevent this.

Big Brother Bezos and Amazon's Alexa, Blink, Echo, Eero, Fire, Kindle, Ring
By Duane Thresher, Ph.D. December 7, 2021
1984 was published by George Orwell (pen name of Eric Arthur Blair) in 1949. It describes a world where society is run by a totalitarian government; actually three police states pretending, by mutual agreement, to continually be at war with one or another so they can deny individual rights by claiming a protective state of emergency, like has been done with Coronavirus. To further control the populace, privacy has been destroyed by installing cameras, microphones, screens, and speakers everywhere, including in every room of everyone's home, so that, at all times, everyone can be told what to think and everything everyone says or does can be known by the government, represented by a man known as Big Brother, to make it seem protectively familial. Signs everywhere say "Big Brother Is Watching You". Orwell, in 1949, clearly meant this as a condemnation of the Soviet Union (now Russia), represented by mass-murderer Chairman Joseph Stalin, but there has been much speculation about who this could be these days. I have myself on Apscitu speculated that Big Brother could be Google, represented by Russian-born Google founder Sergey Brin, particularly given Google's collaboration with the National Security Agency (NSA) to invade the privacy of Americans. Here though, just in time for Christmas, I describe how Big Brother could be Amazon, represented by founder Jeff Bezos, given Amazon's heavily-advertised privacy invasion system of, from A to Z (Amazon's logo), Alexa, Blink, Echo, Eero, Fire, Kindle, and Ring, as well as given its collaboration with the NSA and other agencies.

CISA: No Infrastructure Cybersecurity, Just a Stepping Stone for IT Incompetents
By Duane Thresher, Ph.D. November 8, 2021
As the name implies, the Cybersecurity and Infrastructure Security Agency (CISA), part of the Department of Homeland Security, is the main U.S. Government agency responsible for infrastructure cybersecurity. This includes elections, for which CISA is already rightfully notorious and which I've investigated, and electrical, including nuclear, power plants, which CISA has ignored and I've written about in Handing Over America's Electrical Grid to the Russians and Nuclear 9/11, for example. As history shows, those in CISA are always IT incompetent, incapable of doing infrastructure cybersecurity and protecting America, and only concerned with using CISA as a stepping stone to even higher-paying jobs. Stop this dangerous national security IT incompetence — remember 9/11 Was Due to IT Incompetence — and let me, Dr. Duane Thresher, CEO of Apscitu Inc. and a real IT expert, do America's infrastructure cybersecurity.

Hacking and Forced Meltdown of Nuclear Power Plants: Upwind of Washington, Baltimore, Philadelphia
By Duane Thresher, Ph.D. September 21, 2021
In Nuclear 9/11, I wrote again about the hacking and forced meltdown of nuclear power plants, which Russia would love to attack the U.S. with since it also proves that a catastrophic meltdown like Chernobyl in 1986 can't only happen to them. I focused on Southern Nuclear power plants, which are in Georgia and Alabama, and their dangerous IT incompetent CIOs: current Russian-ransomwared Colonial Pipeline woman CIO Marie Mouchet and current Southern Nuclear black CIO Martin Davis. The U.S. Government, whose main reason for existence is to protect us from such an attack, cares only about the sex and race (euphemistically, diversity) of those, like CIOs, who are supposed to protect us from cyberattack, not about their competence. Worse for the South, the U.S. Government, based in the North around Washington DC, still, since the Civil War, considers the South an enemy to be destroyed and is fine with any catastrophes befalling it — Hurricane Katrina and New Orleans for example — including the horrible death of hundreds of thousands by radiation sickness. However, the U.S. Government should realize that it has its own extremely vulnerable nuclear power plants nearby. For example, the already 50 years old, but licensed for another 30 years, Peach Bottom nuclear power plant, which is near, by wind and water, Washington, Baltimore, and Philadelphia, and is already notorious for its lax physical security, has its own dangerous IT incompetent woman CIO, Kelly Lyman. Letting nuclear power become a national security catastrophe is also a catastrophe for the environment, including climate, which the U.S. Government also pretends to care about, because it is the only climate-friendly power that can feasibly meet America's energy needs, as many environmentalists admit. Apscitu can fight to protect America, nuclear power, and the environment.

Nuclear 9/11
By Duane Thresher, Ph.D. September 11, 2021
Today is the 20th anniversary of 9/11. Two years ago I wrote 9/11 Was Due to IT Incompetence, by the U.S. Government, specifically the NSA and CIA, and predicted another mega national security disaster around 10 years after the last, the hacking of the NSA and CIA by Edward Snowden, which was about 10 years after mega national security disaster 9/11. The U.S. Government, and the companies who actually do the U.S. Government's jobs, are incompetent and generals always fight the last war, so their predicting the next possible mega national security disaster is impossible. However, the recent Colonial Pipeline cyberattack by Russia clearly indicates, to non-incompetents, that the next possible mega national security disaster will be via IT. There has been talk of hacking into airliner flight controls and crashing the planes into targets, but again, that is fighting the last war and is actually trivial compared to what can be done — hacking into and forcing the meltdown of nuclear power plants near major cities (all are), about which I have written in Ransomwared Nuclear Power Plants Upwind of Major U.S. Cities. 3000 died in 9/11, but a forced meltdown of a single nuclear power plant would multiply that by 10 or 100 or more, making it a giga national security disaster, and dying from radiation sickness is one of the most horrible ways to die. Speaking of anniversaries and catastrophic nuclear power plant meltdowns, this year is the 35th anniversary of Chernobyl (1986), which the Russians would love to prove is a disaster that can't only happen to them. Apscitu can fight to protect America from a nuclear 9/11.

Dangerous Fraud Kelly Bissell, IT Incompetent Accenture Head CISO
By Duane Thresher, Ph.D. August 27, 2021
Recently, I wrote IT Incompetent Fed IT Company Accenture and CISO Nicole Dean Ransomwared, National Security In Danger, 3 years after I wrote Fed IT Run By Enron's Corrupt Accountant, IT Incompetent Accenture. These focused on IT incompetent Nicole Dean, Accenture Federal Services Chief Information Security Officer (CISO), but with mention of IT incompetent Suzette Kent, former Federal Chief Information Officer (CIO) and former Accenture employee who while Fed CIO swung federal IT services contracts to Accenture, and IT incompetent John Edwards, Central Intelligence Agency CIO and former Accenture employee. Still don't think Accenture is completely IT incompetent and a danger to national security? See IT Hiring: Cascade Failure in Principles of IT Incompetence and consider Kelly Bissell, Accenture Global Cybersecurity Lead, essentially Accenture Head CISO. Bissell lies about his IT expertise — he has none and is an extreme IT incompetent — and has been a part of the fraud that is Accenture since before it called itself Accenture. I am willing to back this in court, in case Kelly Bissell and/or Accenture wants to sue me for defamation. Bissell is a danger to national security because, as he brags on social media, he is giving cybersecurity advice to the U.S. head of national security, including cybersecurity, incompetent President Joe Biden, who already surrendered to Russia in the IT war (cyberwar); see U.S. Surrenders in IT War, Starts Paying Tribute to Russia.

Amazon Covers Up Return of Your Right to Sue Them
By Duane Thresher, Ph.D. July 20, 2021
As I explained in The Decline and Fall of Amazon, Amazon is the quintessential IT company. And it is now, particularly given the Coronavirus Scare causing an irrational fear of going to stores, the most powerful company in history. Thus for better or worse — mostly worse — Amazon has a huge effect on IT law. For the last 10 years, starting under the Amazon-friendly Obama Administration between 6 and 29 Aug 2011 — as proved by the Internet Archive Wayback Machine — Amazon had taken away your right to sue them and replaced it with forced arbitration, which they controlled. Recently though, between 3 and 7 May 2021, under threat from a now Amazon unfriendly Congress and Administration, Amazon returned your right to sue them, mostly. However, fearing a flood of lawsuits, Amazon covertly announced this change to its customers, via a common and usually ignored "terms of service change" email, only on the evening of 19 Jul 2021, the evening before Jeff Bezos, founder and CEO of Amazon, was all over the (gullible) news for his 9 AM 10-minute tourist "space flight" on one of his rockets, on the anniversary of man first landing on the moon on July 20, 1969 and after which Bezos specifically thanked Amazon customers for paying for it. While this cover up worked as planned, you nonetheless can now sue Amazon. I will tell you why you would — Amazon fraudulently selling you used items at new item prices — and how to do so, without a lawyer.

CDC: Clowns of Disease and Data Control
June 12, 2021Since the Coronavirus Scare started with a vengeance, around April Fool's Day 2020, ultimate authority in the United States has been handed over to the unelected officials at the Centers for Disease Control and Prevention (CDC) in Atlanta Georgia, next to the NIH-funded (National Institutes of Health) Yerkes National Primate Research Center, where they experiment on primates (humans are primates). Presidential and gubernatorial executive orders, which are already of questionable constitutionality since they are not mentioned there, about coronavirus restrictions state that Americans have to do whatever the CDC says, even if it contradicts, as it invariably does, what the Constitution's Bill of Rights says federal and state (under the 14th Amendment) governments can not do. See for example

Ransomwared Nuclear Power Plants Upwind of Major U.S. Cities
By Duane Thresher, Ph.D. June 6, 2021
On the 77th anniversary of D-Day, in memory of those who actually fought and died to protect America.
As I emailed to news outlets in the major cities downwind of the very possibly ransomwared nuclear power plants, in summary of U.S. Surrenders in IT War, Starts Paying Tribute to Russia:
You are aware of the Russian-backed hacking and ransomwaring of Colonial Pipeline and the devastating effect on the south and east coast.
The Colonial Pipeline executive responsible for allowing this is IT incompetent Chief Information Officer (CIO) Marie Mouchet, whose only education is as an elementary school teacher. Before she became Colonial Pipeline CIO several years ago she was CIO for Southern Nuclear, which operates three nuclear power plants (currently two reactors each):

U.S. Surrenders in IT War, Starts Paying Tribute to Russia
By Duane Thresher, Ph.D. May 31, 2021
On Memorial Day, in memory of those who actually fought and died to protect America.
Colonial Pipeline Company is a corporation headquartered near Atlanta Georgia, like also-hacked Equifax is. Like most large corporations, it is incorporated in Delaware, to take advantage of their corporate law and proximity to Washington DC. Colonial Pipeline Company's largest shareholder is Koch Industries, the private corporation owned by the Koch brothers, well-known conservative donors. The majority of Colonial Pipeline Company however, is owned by foreigners. Colonial Pipeline owns a critical pipeline, actually two, that runs from a refinery near Houston Texas (been there) up the East Coast to New York City (lived there), through major cities, including Atlanta, or with branches to them, including Richmond Virginia (been and go there) and Washington DC (been and go there). One pipeline carries gasoline, for cars at filling stations, and one pipeline carries diesel fuel, for trucks at filling stations, and jet fuel for airplanes, including directly to major airports along the way. If the flow of Colonial Pipeline is interrupted, transportation in the most densely populated part of the U.S. can be dangerously interrupted. Colonial Pipeline is thus a strategic military target.

Banned-For-Life Trader and Business Insider CEO Henry Blodget Using Fake News for Stock Price Manipulation?
By Duane Thresher, Ph.D. May 5, 2021
After I wrote IT Reporting: Scraping the Bottom of the Barrel with a Fake Facebook Data Breach, I wondered why a major media news outlet like Business Insider would publish fake news about Facebook and risk a multi-million dollar libel lawsuit that Facebook could easily win. Having written Stock Market Crash Deja Vu: Reddit Violates Securities Exchange Act earlier this year, the answer came to mind: Business Insider planned to make at least that much by short selling Facebook stock and driving its price down with the fake news. I then proceeded to mail a complaint of this illegal (Title 15 of U.S. Code, § 78i(a)(2)) stock price manipulation to the Securities and Exchange Commission (SEC), with copies mailed to Facebook and Business Insider. This SEC complaint is particularly important because it has a bearing on the federal government's current ridiculously-weak anti-monopoly case against Facebook: Federal Trade Commission v. Facebook Inc., U.S. District Court for the District of Columbia, Case No. 1:20-cv-03590. After mailing this SEC complaint, I was investigating who else at Business Insider should have their records, particularly emails, subpoenaed to look for evidence of the crime. I discovered that the founder, editor-in-chief, and CEO of Business Insider, Henry Blodget, had been convicted by the SEC of essentially the same securities fraud of stock price manipulation by fake news, been fined $4 million, and been banned for life from the securities industry. Thumbing his nose at and taunting the SEC, Blodget then founded Business Insider, which is the perfect cover for continuing this illegal stock price manipulation.

IT Reporting: Scraping the Bottom of the Barrel with a Fake Facebook Data Breach
By Duane Thresher, Ph.D. April 21, 2021
I've written extensively and expertly about the very sensitive information, perfect for identity theft, that Facebook has about its users: Facebook Reads Your And Government Officials'/Politicians' Email and Facebook Has A Database Of User ID Photos and, most importantly, Insecure Facebook Demands Your Passport, Bank Statements, Medical Records, ... I've also written about how Facebook let hackers have this information in a real data breach (September 2018, 50 million Facebook accounts hacked): Yahoo-Then-Facebook CISO Alex Stamos Allows Yet Another Massive Data Breach. That hackers may have stolen Facebook users' passports, bank statements, and medical records is a big story that the IT incompetent media completely missed. Instead, this month the IT incompetent media, particularly "journalists" with failing careers, have been hyping a fake Facebook data breach: half a billion Facebook users had their Facebook information, particularly phone numbers, "stolen" in a "data breach" that will lead to identity theft of a large percentage of the world's population. The IT incompetent failing liberal media has completely misunderstood what really happened and sensationalized the non-story to boost sales and careers and force their liberal political ideology on people, just as they did in the "Facebook-Cambridge Analytica data scandal", another fake Facebook data breach. What happened was everyday perfectly-legal "scraping", which I will expertly explain here and which you benefit from. With reference to Information Technology (IT) Age v. Information Age, I'll explain how Google (the "Googolic Church") and Wikipedia (the "Church Scribes") were part of this IT incompetent failing liberal media frenzy.
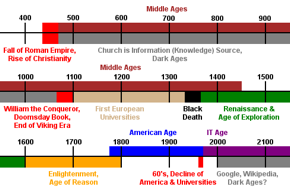
Information Technology (IT) Age v. Information Age
By Duane Thresher, Ph.D. April 12, 2021
Apscitu uses the term Information Technology Age (IT Age) instead of just Information Age, as created and hyped by the IT incompetent and history ignorant media, because as history shows, information, a.k.a. knowledge, has been important in all ages, even more than now, not just since the 1970's advent of widespread computer use, which is what Information Age refers to. What has really marked our age is information technology, like computers and, even more important for the spread of information, a.k.a. education, the Internet (actually the Web; for Internet v. Web see Websites: Simple is Smart, Secure, and Speedy), which was created in the early 1990's. However, this technology has actually led to a decline of the importance of information and of the information itself, via Wikipedia, Google, and universities. This decline is just history repeating itself — "those who forget the past are doomed to repeat it" — with Wikipedia and Google as the Church, the source of all information and thus the controllers of it.

Microsoft Guilty But Protected by NSA, AB PAC, India, and DelBenes
By Duane Thresher, Ph.D. March 22, 2021
IT incompetent Microsoft is guilty of The Doomsday Microsoft Government Email Data Breach and Doomsday II: The Massive Microsoft Email Data Breach Sequel and should be in serious, even terminal, legal and public relations/business trouble for it, but remains untouchable. This is because Microsoft is being protected, for several reasons, by those in and closely tied to the federal government. First, Microsoft has become inherent in federal government IT over the decades and it's too late for the federal government to do anything but defend Microsoft, no matter how disastrously IT incompetent they are. Second, Microsoft has colluded with the National Security Agency (NSA) to spy on Americans and is being rewarded for that by the federal government. Third, Microsoft, via its IT incompetent leadership, including those from India, has paid for many elected federal officials. These include U.S. Representative Suzan DelBene from Washington state, home of Microsoft, who used to be a Microsoft executive, and whose husband Kurt DelBene is a longtime Microsoft executive, except for when he was appointed by the federal government to implement HealthCare.gov, which was hacked at implementation; see HealthCare.gov Hacked. While at Microsoft, IT incompetent Kurt DelBene managed both Outlook, implicated in The Doomsday Microsoft Government Email Data Breach, and Exchange, implicated in Doomsday II: The Massive Microsoft Email Data Breach Sequel. Not to mention — and no one does — Microsoft liberally supports the dirty tricks political action committee, AB PAC.

Federal Judiciary Reacts To Hackers: Evidence Tampering OK, Exposing NSA Surveillance Not
By Duane Thresher, Ph.D. March 17, 2021
As I showed in Hackers Own The Federal Legal System, the federal judicial system has been taken over by hackers and the federal judiciary has admitted to this and reacted. Their reaction were orders on Highly Sensitive Documents (HSDs) reworded from a directive by the same IT incompetent agency — the Administrative Office of the United States Courts (AO), particularly its director appointed by the Chief Justice of the Supreme Court — that allowed itself to be hacked in the first place and is responsible for taking care of all documents (evidence documents and court documents), now all electronic, in the federal judicial system. These orders completely ignore the document tampering — to change court decisions — that will now occur, which was the main focus of Hackers Own The Federal Legal System, and only try to keep confidential the documents, HSDs, they consider important. What the AO considers HSDs that they will really try to protect now and non-HSDs that they will leave to the hackers, since they have been hacked permanently and undetectably, is outrageously self-serving. How the AO plans to keep HSDs confidential, when they already have a procedure for sealed and confidential documents that was hacked, is dangerously IT incompetent.

Hackers Own The Federal Legal System
By Duane Thresher, Ph.D. March 12, 2021
One of the most important implications of The Doomsday Microsoft Government Email Data Breach and Doomsday II: The Massive Microsoft Email Data Breach Sequel is that hackers "own" the U.S. federal legal system, which consists of the legal departments and agencies of the executive branch and the entire judicial branch of the federal government. These organizations all used Microsoft email in some way so had their networks of computers hacked into, permanently and undetectably. The very foundation of the legal system, and what is assumed by it, is that police evidence (usually documents) and court documents have not been tampered with, but hackers can now undetectably tamper with these documents at will since these documents are all digital (a.k.a. electronic) and on computers these days. All judicial decisions are now questionable (including in some of my own cases), as some enterprising defense lawyer will soon point out to his guilty client's advantage. It's far worse than even Equifax Dead: Hacked So Credit Reports Worthless. Additionally, many court documents contain sensitive information that could be used to hurt the people involved and is supposed to be kept confidential, and all this is now available to hackers. The only solution is to go back to paper only documents, mailing them, and physical security for them. This will not only make the legal process more secure, but more fair, as guaranteed by the Fifth Amendment right to due process.

Doomsday II: The Massive Microsoft Email Data Breach Sequel
By Duane Thresher, Ph.D. March 8, 2021
Only IT incompetent megacorporation Microsoft could have an oxymoron like Doomsday II, the sequel to the end of the world, in this case the sequel to The Doomsday Microsoft Government Email Data Breach. But perhaps it should be seen as taking doomsday on the road. The first Microsoft email doomsday data breach destroyed U.S. Government IT and the sequel is being called a global crisis, having also destroyed the IT of foreign governments and institutions. At least the IT incompetent media realized this time that it was Microsoft's fault — they call it the Microsoft Exchange Cyberattack — which they didn't last time. The first Microsoft email doomsday data breach was due to Microsoft's Outlook email, in all its various guises, and this sequel Microsoft email doomsday data breach is due to Microsoft's Exchange, which is their email server. Here I explain all this and how they are related.

The Doomsday Microsoft Government Email Data Breach
By Duane Thresher, Ph.D. February 22, 2021
As Apscitu has been warning for years, since its inception, particularly through Stop IT Incompetence, the IT Incompetents Hall Of Shame (Government, Business, and Media), and Apscitu Mail, there has been a doomsday data breach of the federal government's email and (then) networks, and this was due to government IT incompetence, not the supposedly sophisticated foreign government hackers. This doomsday data breach was finally admitted to by the federal government starting in December 2020 and continuing, but may have been going on undetected for many months or even years and may still be going on undetected.
Those who have even a clue about this data breach, which doesn't include the media, are calling it the most massive — and not just yet another most massive — (thus worst) data breach in history, whose vast effects will be the major national security risk for many years into the future, if the United States survives it at all; hence "doomsday data breach". ...

Stock Market Crash Deja Vu: Reddit Violates Securities Exchange Act
By Duane Thresher, Ph.D. February 2, 2021
This article is in honor of Groundhog Day, specifically the movie, where the same day, Groundhog Day, February 2nd, kept happening over and over again. In this case though the repeating day was Black Thursday, October 24th, the start of the Stock Market Crash of 1929. And in this case the villain was Reddit, whose modus operandi was illegal price manipulation of GameStop stock, intentionally leading to a short squeeze on important short sellers like hedge funds, which could have resulted in another stock market crash and ensuing depression, particularly during the Coronavirus Scare. In this case, there are no heroes, except perhaps someone who can clearly explain all this, as I do here, since the mainstream media clearly can't.

Apscitu Puzzle #9 — For Inauguration Day
January 20, 2021A puzzle for Inauguration Day, as well as Halloween.
Download a pdf of Apscitu Puzzle #9 here. For puzzle background and discussion, which may help doing the puzzle, see the March 14, 2020 article, Introducing Apscitu Puzzles, including doing Apscitu Puzzle #1 if you haven't yet.

Announcing The Apscitu Law Website
January 6, 2021Announcing the Apscitu Law website, in support of Apscitu Inc.'s IT law consulting; see Services and Consulting. For more about the website see there the About Apscitu Law page, which also replaces the old Legal page on the Apscitu website. For relevant cases see the Casebook on the Apscitu Law website. The Casebook includes the early foundational cases that established my (Apscitu Inc. CEO Dr. Duane Thresher's) legal expertise and led to Apscitu Inc.'s IT law consulting and the Apscitu Law website. The Casebook will also include later cases, and describe upcoming cases in a blurb at the top of the listing.

Apscitu Puzzle #8 — For Apscitu Law
December 24, 2020A puzzle in honor of Apscitu Law, as well as Apscitu Mail (that's a clue). Apscitu Law makes IT law much less cryptic than this Apscitu Puzzle, titled Legal Name Is An Alias.
Download a pdf of Apscitu Puzzle #8 here. For puzzle background and discussion, which may help doing the puzzle, see the March 14, 2020 article, Introducing Apscitu Puzzles, including doing Apscitu Puzzle #1 if you haven't yet.

MIT Lawyers v. Dr. Thresher
December 7, 2020MIT Lawyers v. Dr. Thresher was my (Dr. Duane Thresher's) fourth case; see Casebook on the Apscitu Law website. It was intertwined with and led to the cases Dr. Thresher v. MIT President Reif et MIT Lawyers and Dr. Thresher v. MIT Lawyer Baletsa. This case was my first as a defendant and happened after I had started Apscitu in Virginia and had long been an MIT alum.
As much as it hurts me to admit, MIT has dramatically decreased in IT excellence, including security — to the point of incompetence — from when I was getting my B.S. in Electrical Engineering and Computer Science there. Like all other universities, they, i.e. non-MIT-alum MIT administrators, have traded off academic excellence — to the point of incompetence — for political correctness, particularly diversity. This incompetence has led to corruption. I cannot help but to try to fight all this, if just in protecting MIT's reputation I protect my own a little. Thus for years I have been fighting MIT about its political correctness, IT incompetence, particularly regarding email and security, and more recently corruption.

Dr. Thresher v. Montana
December 2, 2020Dr. Thresher v. Montana was my (Dr. Duane Thresher's) third foundational case; see IT Law Expertise in my Credentials on the Apscitu website and About Apscitu Law and Casebook on the Apscitu Law website. Actually, it wasn't just one case — living and running a business in Montana led to numerous cases. Montana is perpetually at the top of the list of most corrupt states and this is well-earned. A big part of the reason for this rampant corruption is that Montana is full of incompetents, particularly IT incompetents (but also lawyers, etc.); see Principles of IT Incompetence (IT Hiring: IT Incompetence Breeds Disloyalty and Corruption).

Dr. Thresher v. Prof. Bedell
November 18, 2020Dr. Thresher v. Prof. Bedell was my (Dr. Duane Thresher's) second foundational case; see IT Law Expertise in my Credentials on the Apscitu website and About Apscitu Law and Casebook on the Apscitu Law website. This case started while I was working as a network engineer at the Arctic Region Supercomputing Center in Alaska, where I did some research and work on cellular telephony (which itself involves important IT law issues). When I then started my own business, Thresher Networks LLC, in Montana, I continued this cellular telephony research, including buying from Amazon.com a just-published book, Wireless Crash Course — A Real World Perspective, Third Edition, by Paul Bedell, published by McGraw-Hill, Steve Chapman editor. Paul Bedell was/is a professor at DePaul University in Chicago, in the College of Computing and Digital Media, whose dean was/is Dr. David Miller, and used/uses the book in his courses.

Dr. Thresher v. Prof. Dr. Lohmann
November 17, 2020Dr. Thresher v. Prof. Dr. Lohmann was my (Dr. Duane Thresher's) first foundational case; see IT Law Expertise in my Credentials on the Apscitu website and About Apscitu Law and Casebook on the Apscitu Law website. This case was from when I was still in academia, doing research at the Alfred Wegener Institute (AWI) in Germany. My wife, Dr. Claudia Kubatzki, and I worked for Prof. Dr. Gerrit Lohmann, in his climate modeling group.
Evidence in this case can be found in the article I wrote about it, Corrupt German Climate Science, for my controversial website, RealClimatologists.org (see Climate of Incompetence), particularly in the lawyer email thread referred to in that article.

FOIA: That's Some Exemption, That Exemption 6
By Duane Thresher, Ph.D. November 11, 2020
I file a lot of Freedom Of Information Act (FOIA) requests. Many are to discover the outrageous salaries of IT incompetent government IT officials for the Government IT Incompetents Hall Of Shame (ITIHOS). These are usually successful, although after many months. But some are for Apscitu Mail, to discover the government email addresses (.gov) of government officials, which is part of my preparation for a lawsuit against the U.S. Government for violation, in its use of email, of my First Amendment right "to petition the Government for a redress of grievances". These are usually not successful, because of Exemption 6 of the FOIA law (Title 5 of the United States Code, § 552(b)(6)). If you actually read Exemption 6 though, you realize it's ridiculous to say it applies to government email addresses. The whole situation is as surreal as Catch-22, which I read as a teenager and later saw the movie. I play Yossarian, instead of Alan Arkin, and the U.S. Government plays itself, again.

IT Incompetent Attorneys General v. Google
By Duane Thresher, Ph.D. November 7, 2020
A few days before Halloween, U.S. Attorney General William Barr announced that he and the attorneys general (AG) of eleven states were filing a civil lawsuit against Google in U.S. District Court (the lowest federal court, where all federal cases must start) of the District of Columbia (where conveniently Google has a corporate presence) for violating the Sherman Antitrust Act of 1890 (Title 15 of the United States Code, §§ 1-7). While Google is a prime candidate for an anti-monopoly lawsuit, given the IT incompetence of all the attorneys general and the IT incompetent track record of the U.S. Attorney General, and his Department of Justice, in antitrust lawsuits against IT corporations, this will take years and cost millions of dollars, and result in no real help to Google's victims.

Apscitu Puzzle #7 — For Election Day
November 3, 2020A puzzle for Election Day, as well as Halloween.
Download a pdf of Apscitu Puzzle #7 here. For puzzle background and discussion, which may help doing the puzzle, see the March 14, 2020 article, Introducing Apscitu Puzzles, including doing Apscitu Puzzle #1 if you haven't yet.

Apscitu Puzzle #3 — For Incompetent Corrupt Government Officials
May 15, 2020A puzzle to mark the day when I finally overcame obstructions by Virginia Governor Ralph Northam and U.S. District Court Judge David J. Novak and served a summons on Northam in my case against him for violation of my First Amendment right to peaceably assemble, even during the Coronavirus Scare: Dr. Duane Thresher v. Governor of Virginia Ralph Northam. I had the summons served by going, without a mask, to Richmond, where both Northam and Novak work, and waiting while the Richmond Office of the Sheriff served the summons on Governor Northam.
Download a pdf of Apscitu Puzzle #3 here. For puzzle background and discussion, which may help doing the puzzle, see the March 14, 2020 article, Introducing Apscitu Puzzles, including doing Apscitu Puzzle #1 if you haven't yet.

Proofpoint Investigation: Fraud and Government Email Tampering
By Duane Thresher, Ph.D. January 10, 2020
The research for Net Neutrality: Who Controls the Communications of the Communications Controllers? led to further investigation of Proofpoint Inc., the IT incompetent email service provider for the IT incompetent Federal Communications Commission (FCC). It was discovered that Proofpoint is also the email service provider for the IT incompetent Department of Commerce (DOC) and that Proofpoint is illegally reading and blocking emails from people trying to contact both the FCC and the DOC based on Proofpoint's own arbitrary criteria, probably political or profit-seeking. Moreover, it was discovered that Proofpoint's Cybersecurity Executive Vice President (EVP), Ryan Kalember, is an IT incompetent fraud who has widely lied about his qualifications.

Net Neutrality: Who Controls the Communications of the Communications Controllers?
By Duane Thresher, Ph.D. August 10, 2019
Answer: Proofpoint Inc. of Sunnyvale California, just minutes down the road from Google, Facebook, and Twitter. The question more specifically: Who controls the email of the Federal Communications Commission (FCC)? Your question: What does this have to do with net neutrality? My answer: Read on.
The Internet in the United States has a backbone. It's fiber optic cables able to carry massive amounts of data, starting with voice, across the country (note: I'm a certified fiber optic technician). These fiber optic cables, or at least their copper predecessors, were laid by AT&T back when it was a government-authorized monopoly — so could more easily get rights-of-way, the most valuable asset — long before the Internet started in the early 1990s.
FBI Hacking Investigation Negligence Lawsuit
By Duane Thresher, Ph.D. February 22, 2018
My family and I, particularly our young daughter, were the victims of not one but two(!) health insurance company data breaches: Montana Department of Public Health and Human Services and Premera Blue Cross. At the time (2013 – 2015) these were two of the worst data breaches ever.
It was officially pretended that identity theft was the only concern from these so only cheap credit monitoring (probably using the now-hacked Equifax) for a couple of years needed to be offered as a remedy. However, child abductors, including pedophiles, find this information invaluable since it includes names, addresses and medical records, which is personal information that greatly aids a child abductor.
